- Efi Profile Editor Free
- Efi File Editor
- Efi Profile Editor Software
- Windows Efi Editor
- Bcd Editor Efi
- Efi Profile Editor
In this article, I will describe steps needed to start on with development of real UEFI applications on x86 PC, and share some practical experiences with problems doing so.I will focus on 64-bit version of UEFI, because the 32-bit version isn't much used in this area (most likely due to Microsoft decision not to support UEFI in 32-bit Vista).So, to follow some of my steps here, you'll need a 64-bit CPU (but not 64-bit OS, youcan use any 32-bit OS as well). We will finish this article with EFI Hello World application.
This article is continuation of my previous article Introduction toUEFI.Make sure to understand things described there, before reading on.
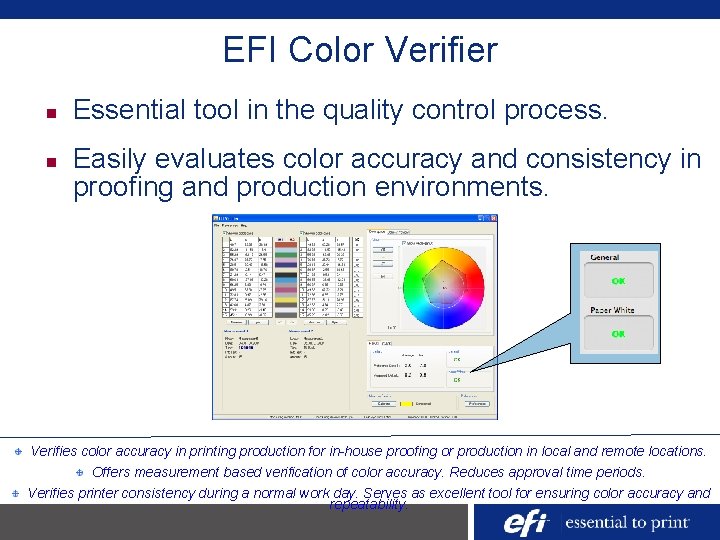
Profile settings do not affect the content of the profile. Fiery Command WorkStation. Hide or show navigation Previous topic Next topic Share Print PDF. Edit profile settings. Profile settings are attributes that determine how the Fiery server uses the profile. For example, you can assign a description or media type to a profile. It supports full BIOS image parsing including the flash descriptor or any binary files containing UEFI volumes; it is compatible with multiple BIOS image types, including ROM, BIN, FD, CAP, BIO, WPH, and EFI, all of which will be conveniently loaded and displayed alongside pertinent details including name, type/subtype, and text for example. VirtualBox, for instance, supports EFI, so it's possible to install Linux under EFI on VirtualBox and use it for testing EFI applications compiled in the host environment. This procedure at least obviates the need to re-start your editor or IDE after every test of your program. If your system is running on UEFI, follow these steps to unhide the EFI system partition, but do not do anything with it. For safety, do not even open this partition. Open Command Prompt as Admin 2. Type diskpart 3. Select disk 0 5. List partition 6. Select partition EFI System Partition Number 7. Assign letter=Choose a.
Of course, anything you try according to this article, you are doing at your own risk.
Getting the hardware
To start UEFI development, first of all you need to get a motherboard whose BIOS has UEFI support.(more precisely we should probably say 'whose firmware has UEFI support', but I will use this form).Finding whether particular BIOS has UEFI support often turns out to be quite complicated task.Motherboard manufacturers license BIOS from other companies, usually from AMI (Aptio, AMIBIOS), Phoenix (SecureCore, TrustedCore, AwardCore) or Insyde (InsydeH20). Forget about determining UEFI support just by end-user stats you see in most shops. Since UEFI support is still only in somewhatexperimental state, in many cases it isn't even listed in motherboard technical specification. In such case you are left to googling and asking on forums, where you often get only internal brand name that is often hard to match with end-user product designation.
One trick that I found out to work for Intel boards (but it may very well work for other boards as well) is to look at BIOS Update Release Notes, e. g. the document which lists changes and fixes of BIOS. If board has UEFI support, you will probably find UEFImentioned there (and only there in case of Intel).
In short, determining UEFI support is much harder than it may seem. Some machines that have this technology are listed here.I use Intel DG33BU board (it was marketed as Intel DG33BUC for some reason).
You will also need some place to boot from. In theory just USB pen should be enough, but inpractice none of 4 brands I tried worked with my board's UEFI implementation. So you may have to use harddrive. I strongly suggest IDE drive, because SATA drives may need some tweaking ofBIOS settings, or they may not work at all. Like the USB pens, USB keyboard might be a problemtoo. I wouldn't fear this that much, but if you can use PS/2 keyboard, do so.
Getting the software
To go on with UEFI development, you will need two developmentpackages: EFI Development Kit (EDK) andEFI Toolkit.
First package, the EFI Development Kit contains the TianoCore (public part of reference UEFI implementation by Intel) source code, along with many examples and binaries of EFI Shell (we'll talk about this later), all ready to be built with nice make system. It even can be built into a Win32 UEFI emulator for more convinient development and testing, but I won't cover that here. I also won't demonstrate usage of EDK build system in this article. Even though it might be a good idea for real world project, I want to give you bit more insight about what goes 'under the hood' here.
Second package, the EFI Toolkit is set of extra UEFI applications like FTP client, Python port, text editor, etc. Strictly speaking, we don't really need this, but it has a set of C headers that is somewhat easier to use than those of EDK (unless you take advantage of EDK build system for your project). However, note that it doesn't contain all headers yet - you will quickly run into this problem if you try some real development with it.
Along with headers, you also will need documentation of the UEFI interface. That can be downloadedafter filling simple form at http://www.uefi.org/specs.This is the official UEFI specification.
Except for UEFI specification, there is also another document called Platform Initialization Specification. This describes implementation of UEFI initialization stages (before drivers areloaded and applications can be executed), and more importantly for us, it also describes interfaceof routines used to implement UEFI. We can understand this Platform Initialization Specification asdescription of Tiano UEFI implementation. It provides more lowlevel control than UEFI, in cases when such control is needed. Strictly speaking, someone may implement UEFI Specification without implementing anything from Platform Initialization Specification, but that's not very likelyto happen in real world.
Last but not least, you will need 64-bit C compiler. I suggest Microsoft Visual C++, whose 64-bit version is freely available in Windows DDK. You can get it here.
Booting into EFI Shell
Up to this point, you may have lacked any visual idea about UEFI. It was just a programatic interface,after all. Purpose of this chapter would be to overcome this, by booting the so-called EFI Shell. EFI shell is much like any other shell you know: you have a command line, through which you can entercommands to browse disk, run applications, configure system, etc. Only difference is that EFI shell is only built using UEFI services, and as such it doesn't require any operating system to run. Working in EFI shell feels much like working in some very simple operating system. From this shell you will also run your applications (later in this article).
Actual steps of booting EFI shell might vary a lot among different BIOS brands. Some BIOSes (mostlyon MACs where EFI is the primary standard) have extra options for specifying file to boot, or caneven have EFI shell built-in inside ROM. However, I only have experience with non-MAC Intel UEFI implementation,that only seems to support the very minimum of features required to install EFI versions of Windows. Microsoft requirementson UEFI implementation, among other things, specify that UEFI boot loader must use fixed path to fileto boot, and if it can't boot UEFI for some reason, it must silently switch to default boot. Thatcauses lot of headache when your UEFI doesn't boot as it should, and you must find out what theproblem is without any information from loader.
For 64-bit UEFI implementations, the path to file that is booted isEFIBOOTBOOTX64.EFI. UEFIboot loader searches all filesystems it can access for this file, and when it finds it, it is executed. As I already said, if the file isn't found, booting continues with legacy BIOS. UEFI boot loader can read MBR or GPT partition tables, and can only read FAT32 partitions. This includes USB drives, so it is possible to boot EFI shell from FAT32-formatted USB pen. Unfortunately, in my tests 3 of 4 USB pens didn't work, and the 4th stopped working too after BIOS update. I had similar problemwith one of two SATA drives not working with UEFI. Therefore, I strongly suggest to use IDE drive, if you have any problems. If you already have at least one FAT32 partition on your drive, you can use it, otherwise you need to create fresh new one.
Now you need to copy binary of EFI shell to that partition. You can find 64-bit binary of EFI shellin EFI Development Kit: {EDK}OtherMaintainedApplicationUefiShellbinx64Shell_full.efi. Copyit to your FAT32 partition as EFIBOOTBOOTX64.EFI.
Now reboot, and enter into BIOS settings. In the Boottab, you should see an UEFI Boot option,enable it. If everything is allright (likely not), now after reboot you should end up in theEFI Shell. If you did, congratulations. If you didn't, and instead your regular OS booted as usual,it most likely means that UEFI boot manager wasn't able to access the drive.
First try to enter Boot Menu during BIOS screen (F10 on my machine). If the EFI Shell on FAT32 partition was detected, but didn't boot, you will see it as one of option (in my case [Internal EFI Shell--Harddrive]). If you see it, just run it. This might possibly happen if you already have some EFI operating system installed, and it has written itself as default EFI boot entry to NVRAM.
Efi Profile Editor Free
If you don't see EFI Shell in the Boot Menu, it means UEFI Boot Loader wasn't able to find any FAT32 drive with EFIBOOTBOOTX64.EFI. If you are trying to boot EFI shell from USB key, try tweakingUSB emulation settings in BIOS. Same applies to SATA disks and SATA/IDE settings. If none of settingswork, or your machine failed to boot from IDE drive, I can't help you any more than to doublecheckeverything I wrote so far (especially typos in path to EFI shell).
If you have some experience with booting EFI shell not covered in thischapter, please drop me amessage, so I can update this article.
Building an UEFI application
So, we are in EFI shell. That means we can finally test any (64-bit) EFI application we write. Time to start writing one. We will of course write and compile applications in normal operating system,not in EFI shell.
EFI application or driver is just a plain Windows PE DLL file, just with different subsystem valuein header. There are 3 new values: EFI application = 10, EFI boot service driver = 11, efi runtime driver = 12 (numbers are decimal). Question how to set subsystem will be answered later, for nowlet's focus on the DLL file.
EFI PE application doesn't have any fancies we have in Windows PEs, like symbol tables, exports, static exception handling data, etc. It does not even have imports - all you will ever need in EFI application ispassed as argument to entry point function. Only thing needed apart from data and code are relocations.So, this is simplest EFI application:
Compiling it with MS Visual C (supply your own path to EFI toolkit):
Here we set path to common EFI headers, and to platform-specific EFIheaders. The /c switch disables linking (we will link separately for better readability), and /Zl disables dependency on defaultlibc libraries.
Linking:
The /entry:main overrides default libc entry point to ourmain() function. The /dll forces creation of relocations. And the IGNORE:4086 disables warningLNK4086, that is caused by nonstandard main() arguments.
Now we have windows DLL, we just need to change PE subsystem value to EFI. For that, EFI Toolkit containssimple (buggy) utility that changes subsystem to one of 3 EFI values. We find this utility inEFI_Toolkitbuildtoolsbinfwimage.exe. To set subsystem to EFI app, we'll use it like this:
Produced file hello.efi should now be functional empty EFI application. We just need to copy it toour FAT32 partition, reboot to EFI shell, and test it:
If we don't get any error message, application worked.
UEFI Programming
Efi File Editor
Now we finally can get deeper into UEFI programming. Your main source for this information should bethe UEFI specification, I will only sum up most basic points.
First of all, we should know something about environemnt of UEFI applications. I will describe onlyenvironment of 64-bit x86 UEFI here (other to be found in UEFI specification).
UEFI runs in uniprocessor flat 64-bit long mode. Usually UEFI runs with memory mapping disabled (physical RAM address = virtual RAM address), but since 64-bit x86 mode requires mapping to be enabled, UEFI maps entire memory so that virtual address is same as physical (i. e. mapping is transparent). Calling convention is usual 64-bit fastcall (first4 arguments in RCX, RDX, R8,R9 with space reserved on stack; rest of arguments passedby stack; RAX, R10, R11 andXMM0-XMM5 notpreserved by called function), so you don't need to worry about special compiler settings. Notable featureof EFI is that for every supported architecture, it defines exact binary interface (ABI).
Now let's look at how our application interacts with UEFI services. First, UEFI provides set of services, called Boot Services. These are available to EFI drivers,applications, and to OS boot loader during boot. At some point during OS booting, OS loader candecide to drop them, and after that point those services become unavailable. There is also a littlenumber of services that always remain available, called 'Runtime Services'. Apart from these twosets of services, all that UEFI offers is available through so-called protocols. Protocol is verymuch like a class in object oriented programming. UEFI defines set of protocols itself (for exampleprotocols handling USB, filesystem, compression, network, …), and application can define itsown protocols (hence the 'Extensible' in 'Unified Extensible Firmware Interface'). Protocols are identified by GUID (Global Unique Identifier, google it if you don't know what it is). Only very fewprotocols are mandatory in UEFI specification, and all the rest may or may not be implemented inparticular firmware. If protocol isn't implemented in firmware, you can load a driver that implements it, or even write such driver yourself.
Now let's look at how to access these services. As I already explained, all you ever need is passed as argument to entry point function. Prototype of entry point function looks like this:
First argument is handle of our process, nothing extra to say about it. Second is pointer to EFI_SYSTEM_TABLE, the top-level EFI structure, which keeps references to everything there is:boot/runtime services, drivers, protocol implementations, memory maps, etc. It is good ideato always save both these arguments in a global variable, so you can access them from anywherein source code. You can find detailed description of EFI System Table in UEFI Specification chapter 4 - EFI System Table. Its C definition looks like this:
Here we see references to boot and runtime services, three standard I/O handles (as implementationsof SIMPLE_TEXT_OUTPUT and SIMPLE_INPUTprotocols), and pointer to ConfigurationTable. Configuration Table holds references to all otherprotocol implementations currently active in system.
First we will show example of using Boot Service. The EFI_BOOT_SERVICES is just a structure that holds pointers to functions described in UEFI Specification chapter 6: Services - Boot Services. For nowwe will use only simple Exit() function, that terminates current EFI application immediately.
Now, we will show simple Hello World application, using the ConOut implementation of SIMPLE_TEXT_OUTPUTprotocol. This protocol is described in UEFI Specification chapter 11.4 - Simple Text Output Protocol.Its C header looks like this:
We are of course interested in OutputString() function, whose prototype is:
Note that UEFI uses Unicode strings only, hence the CHAR16 *String. This pointer meaning is exactly same as in any object oriented programming. With this info, we should be ableto write Hello World app easily:
Also note that UEFI uses CRLF line terminators (rn) instead of just LF (n), and when weuse native EFI functions, there is no layer which reinterprets LF to CRLF. Normally, applications use additional library called EFILIB which does the LF->CRLF transform.
UEFI Programming with FASM
As an extra, I will also demonstrate same Hello World example inassembly (using FASM, thatcurrently has experimental UEFI support since version 1.67.28):
First we need some to create simple UEFI headers (efi.inc):
And here is the assembly code itself (hello.asm):
Compile and link it with fasm.exe hello_world.asm.
That's all for now, hope you enjoyed yourselves.
Comments
Continue to discussion board.
You can contact the author using e-mail vid@x86asm.net.
Visit author's home page.
Revisions
(dates format correspond to ISO 8601)
-->A companion to About Azure Active Directory B2C, this article provides a more in-depth introduction to the service. Discussed here are the primary resources you work with in the service, its features. Learn how these features enable you to provide a fully custom identity experience for your customers in your applications.
Azure AD B2C tenant
In Azure Active Directory B2C (Azure AD B2C), a tenant represents your organization and is a directory of users. Each Azure AD B2C tenant is distinct and separate from other Azure AD B2C tenants. An Azure AD B2C tenant is different than an Azure Active Directory tenant, which you may already have.
The primary resources you work with in an Azure AD B2C tenant are:
- Directory - The directory is where Azure AD B2C stores your users' credentials, profile data, and your application registrations.
- Application registrations - Register your web, mobile, and native applications with Azure AD B2C to enable identity management. You can also register any APIs you want to protect with Azure AD B2C.
- User flows and custom policies - Create identity experiences for your applications with built-in user flows and fully configurable custom policies:
- User flows help you quickly enable common identity tasks like sign-up, sign-in, and profile editing.
- Custom policies let you build complex identity workflows unique to your organization, customers, employees, partners, and citizens.
- Sign-in options - Azure AD B2C offers various sign-up and sign-in options for users of your applications:
- Username, email, and phone sign-in - Configure your Azure AD B2C local accounts to allow sign-up and sign-in with a username, email address, phone number, or a combination of methods.
- Social identity providers - Federate with social providers like Facebook, LinkedIn, or Twitter.
- External identity providers - Federate with standard identity protocols like OAuth 2.0, OpenID Connect, and more.
- Keys - Add and manage encryption keys for signing and validating tokens, client secrets, certificates, and passwords.
An Azure AD B2C tenant is the first resource you need to create to get started with Azure AD B2C. Learn how to:
- Create an Azure Active Directory B2C tenant.
Accounts in Azure AD B2C
Azure AD B2C defines several types of user accounts. Azure Active Directory, Azure Active Directory B2B, and Azure Active Directory B2C share these account types.
- Work account - Users with work accounts can manage resources in a tenant, and with an administrator role, can also manage tenants. Users with work accounts can create new consumer accounts, reset passwords, block/unblock accounts, and set permissions or assign an account to a security group.
- Guest account - External users you invite to your tenant as guests. A typical scenario for inviting a guest user to your Azure AD B2C tenant is to share administration responsibilities.
- Consumer account - Accounts that are managed by Azure AD B2C user flows and custom policies.
Figure: User directory within an Azure AD B2C tenant in the Azure portal
Consumer accounts
With a consumer account, users can sign in to the applications that you've secured with Azure AD B2C. Users with consumer accounts can't, however, access Azure resources, for example the Azure portal.
A consumer account can be associated with these identity types:
- Local identity, with the username and password stored locally in the Azure AD B2C directory. We often refer to these identities as 'local accounts.'
- Social or enterprise identities, where the identity of the user is managed by a federated identity provider. For example, Facebook, Microsoft, ADFS, or Salesforce.

A user with a consumer account can sign in with multiple identities. For example username, email, employee ID, government ID, and others. A single account can have multiple identities, both local and social.
Figure: A single consumer account with multiple identities in Azure AD B2C
For more information, see Overview of user accounts in Azure Active Directory B2C.
Local account sign-in options
Azure AD B2C provides various ways in which users can authenticate a user. Users can sign-in to a local account, by using username and password, phone verification (also known as password-less authentication). Email sign-up is enabled by default in your local account identity provider settings.
Learn more about sign-in options or how to set up the local account identity provider.

User profile attributes
Azure AD B2C lets you manage common attributes of consumer account profiles. For example display name, surname, given name, city, and others.
You can also extend the Azure AD schema to store additional information about your users. For example, their country/region of residency, preferred language, and preferences like whether they want to subscribe to a newsletter or enable multi-factor authentication. For more information, see:
Sign-in with external identity providers
You can configure Azure AD B2C to allow users to sign in to your application with credentials from social and enterprise identity providers. Azure AD B2C can federate with identity providers that support OAuth 1.0, OAuth 2.0, OpenID Connect, and SAML protocols. For example, Facebook, Microsoft account, Google, Twitter, and AD-FS.
With external identity provider federation, you can offer your consumers the ability to sign in with their existing social or enterprise accounts, without having to create a new account just for your application.
On the sign-up or sign-in page, Azure AD B2C presents a list of external identity providers the user can choose for sign-in. Once they select one of the external identity providers, they're taken (redirected) to the selected provider's website to complete the sign in process. After the user successfully signs in, they're returned to Azure AD B2C for authentication of the account in your application.
To see how to add identity providers in Azure AD B2C, see Add identity providers to your applications in Azure Active Directory B2C.
Identity experiences: user flows or custom policies
In Azure AD B2C, you can define the business logic that users follow to gain access to your application. For example, you can determine the sequence of steps users follow when they sign in, sign up, edit a profile, or reset a password. After completing the sequence, the user acquires a token and gains access to your application.
In Azure AD B2C, there are two ways to provide identity user experiences:
User flows are predefined, built-in, configurable policies that we provide so you can create sign-up, sign-in, and policy editing experiences in minutes.
Custom policies enable you to create your own user journeys for complex identity experience scenarios.
The following screenshot shows the user flow settings UI, versus custom policy configuration files.
Read the User flows and custom policies overview article. It gives an overview of user flows and custom policies, and helps you decide which method will work best for your business needs.
User interface
In Azure AD B2C, you can craft your users' identity experiences so that the pages are shown blend seamlessly with the look and feel of your brand. You get nearly full control of the HTML and CSS content presented to your users when they proceed through your application's identity journeys. With this flexibility, you can maintain brand and visual consistency between your application and Azure AD B2C.

For information on UI customization, see:
Custom domain
You can customize your Azure AD B2C domain in the redirect URLs for Azure AD B2C. Custom domain allows you to create a seamless experience so that the pages are shown blend seamlessly with the domain name of your application.
From the user's perspective, they remain in your domain during the sign-in process rather than redirecting to the Azure AD B2C default domain .b2clogin.com. For more information, see Enable custom domains.
Localization
Language customization in Azure AD B2C allows you to accommodate different languages to suit your customer needs. Microsoft provides the translations for 36 languages, but you can also provide your own translations for any language. Even if your experience is provided for only a single language, you can customize any text on the pages.
See how localization works in Language customization in Azure Active Directory B2C.
Email verification
Azure AD B2C ensures valid email addresses by requiring customers to verify them during the sign-up, and password reset flows. It also prevents malicious actors from using automated processes to generate fraudulent accounts in your applications.
You can customize the email to users that sign up to use your applications. By using the third-party email provider, you can use your own email template and From: address and subject, as well as support localization and custom one-time password (OTP) settings. For more information, see:
Add your own business logic
If you choose to use custom policies, you can integrate with a RESTful API in a user journey to add your own business logic to the journey. For example, Azure AD B2C can exchange data with a RESTful service to:
- Display custom user-friendly error messages.
- Validate user input to prevent malformed data from persisting in your user directory. For example, you can modify the data entered by the user, such as capitalizing their first name if they entered it in all lowercase.
- Enrich user data by further integrating with your corporate line-of-business application.
- Using RESTful calls, you can send push notifications, update corporate databases, run a user migration process, manage permissions, audit databases, and more.
Loyalty programs are another scenario enabled by Azure AD B2C's support for calling REST APIs. For example, your RESTful service can receive a user's email address, query your customer database, then return the user's loyalty number to Azure AD B2C.
The return data can be stored in the user's directory account in Azure AD B2C. The data then can be further evaluated in subsequent steps in the policy, or be included in the access token.
You can add a REST API call at any step in the user journey defined by a custom policy. For example, you can call a REST API:
- During sign-in, just before Azure AD B2C validates the credentials
- Immediately after sign-in
- Before Azure AD B2C creates a new account in the directory
- After Azure AD B2C creates a new account in the directory
- Before Azure AD B2C issues an access token
To see how to use custom policies for RESTful API integration in Azure AD B2C, see Integrate REST API claims exchanges in your Azure AD B2C custom policy.
Protocols and tokens
For applications, Azure AD B2C supports the OAuth 2.0, OpenID Connect, and SAML protocols for user journeys. Your application starts the user journey by issuing authentication requests to Azure AD B2C. The result of a request to Azure AD B2C is a security token, such as an ID token, access token, or SAML token. This security token defines the user's identity within the application.
For external identities, Azure AD B2C supports federation with any OAuth 1.0, OAuth 2.0, OpenID Connect, and SAML identity providers.
The following diagram shows how Azure AD B2C can communicate using various protocols within the same authentication flow:
- The relying party application starts an authorization request to Azure AD B2C using OpenID Connect.
- When a user of the application chooses to sign in using an external identity provider that uses the SAML protocol, Azure AD B2C invokes the SAML protocol to communicate with that identity provider.
- After the user completes the sign-in operation with the external identity provider, Azure AD B2C then returns the token to the relying party application using OpenID Connect.
Application integration
When a user wants to sign in to your application, the application initiates an authorization request to a user flow- or custom policy-provided endpoint. The user flow or custom policy defines and controls the user's experience. When they complete a user flow, for example the sign-up or sign-in flow, Azure AD B2C generates a token, then redirects the user back to your application.
Multiple applications can use the same user flow or custom policy. A single application can use multiple user flows or custom policies.
For example, to sign in to an application, the application uses the sign up or sign in user flow. After the user has signed in, they may want to edit their profile, so the application initiates another authorization request, this time using the profile edit user flow.
Multi-factor authentication (MFA)
Efi Profile Editor Software
Azure AD B2C multi-factor authentication (MFA) helps safeguard access to data and applications while maintaining simplicity for your users. It provides extra security by requiring a second form of authentication, and delivers strong authentication by offering a range of easy-to-use authentication methods.
Your users may or may not be challenged for MFA based on configuration decisions that you can make as an administrator.
See how to enable MFA in user flows in Enable multi-factor authentication in Azure Active Directory B2C.
Conditional Access
Azure AD Identity Protection risk-detection features, including risky users and risky sign-ins, are automatically detected and displayed in your Azure AD B2C tenant. You can create Conditional Access policies that use these risk detections to determine remediation actions and enforce organizational policies.
Azure AD B2C evaluates each sign-in event and ensures that all policy requirements are met before granting the user access. Risky users or sign-ins may be blocked, or challenged with a specific remediation like multi-factor authentication (MFA). For more information, see Identity Protection and Conditional Access.
Password complexity
During sign up or password reset, your users must supply a password that meets complexity rules. By default, Azure AD B2C enforces a strong password policy. Azure AD B2C also provides configuration options for specifying the complexity requirements of the passwords your customers use.
For more information, see Configure complexity requirements for passwords in Azure AD B2C.
Force password reset
As an Azure AD B2C tenant administrator, you can reset a user's password if the user forgets their password. Or you would like to force them to reset the password periodically. For more information, see Set up a force password reset flow.
Smart account lockout
To prevent brute-force password guessing attempts, Azure AD B2C uses a sophisticated strategy to lock accounts based on the IP of the request, the passwords entered, and several other factors. The duration of the lockout is automatically increased based on risk and the number of attempts.
For more information about managing password protection settings, see Mitigate credential attacks in Azure AD B2C.
Protect resources and customer identities
Azure AD B2C complies with the security, privacy, and other commitments described in the Microsoft Azure Trust Center.
Sessions are modeled as encrypted data, with the decryption key known only to the Azure AD B2C Security Token Service. A strong encryption algorithm, AES-192, is used. All communication paths are protected with TLS for confidentiality and integrity. Our Security Token Service uses an Extended Validation (EV) certificate for TLS. In general, the Security Token Service mitigates cross-site scripting (XSS) attacks by not rendering untrusted input.
Access to user data
Azure AD B2C tenants share many characteristics with enterprise Azure Active Directory tenants used for employees and partners. Shared aspects include mechanisms for viewing administrative roles, assigning roles, and auditing activities.
Windows Efi Editor
You can assign roles to control who can perform certain administrative actions in Azure AD B2C, including:
- Create and manage all aspects of user flows
- Create and manage the attribute schema available to all user flows
- Configure identity providers for use in direct federation
- Create and manage trust framework policies in the Identity Experience Framework (custom policies)
- Manage secrets for federation and encryption in the Identity Experience Framework (custom policies)
For more information about Azure AD roles, including Azure AD B2C administration role support, see Administrator role permissions in Azure Active Directory.
Bcd Editor Efi
Auditing and logs
Azure AD B2C emits audit logs containing activity information about its resources, issued tokens, and administrator access. You can use the audit logs to understand platform activity and diagnose issues. Audit log entries are available soon after the activity that generated the event occurs.
In an audit log, which is available for your Azure AD B2C tenant or for a particular user, you can find information including:
- Activities concerning the authorization of a user to access B2C resources (for example, an administrator accessing a list of B2C policies)
- Activities related to directory attributes retrieved when an administrator signs in using the Azure portal
- Create, read, update, and delete (CRUD) operations on B2C applications
- CRUD operations on keys stored in a B2C key container
- CRUD operations on B2C resources (for example, policies and identity providers)
- Validation of user credentials and token issuance
For more information on audit logs, see Accessing Azure AD B2C audit logs.
Usage analytics
Azure AD B2C allows you to discover when people sign up or sign in to your app, where the users are located, and what browsers and operating systems they use.
By integrating Azure Application Insights into Azure AD B2C custom policies, you can gain insight into how people sign up, sign in, reset their password or edit their profile. With such knowledge, you can make data-driven decisions for your upcoming development cycles.
For more information, see Track user behavior in Azure Active Directory B2C using Application Insights.
Efi Profile Editor
Next steps
Now that you have deeper view into the features and technical aspects of Azure Active Directory B2C, get started with our tutorial for creating an Azure Active Directory B2C tenant.